Intercepting HTTP Traffic for Thick-Client Penetration Testing

Hello folks, I’m Sahil Shah, A Security Researcher passionate about Web, Mobile, and Thick client penetration testing.
In today’s blog, I’ll walk you through intercepting thick client HTTP traffic using Fiddler and Burp Suite with a dual proxy setup. I’ll keep it simple and beginner-friendly, so stay with me
let’s dive in! 🚀
First, you need to install the required tools for this setup.
Install Fiddler : Click the link below and follow the installation instructions to complete the setup.
After completing the installation, the initial interface will look like this.

Enable HTTPS Decryption in Fiddler
Fiddler allows you to intercept and decrypt HTTPS traffic by installing its root certificate.
- Go to Tools → Options → HTTPS
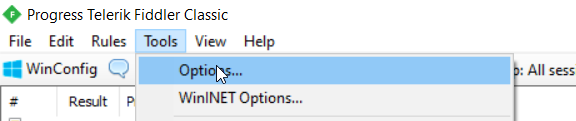
- Check the following options:
✅ Capture HTTPS CONNECTs
✅ Decrypt HTTPS Traffic
✅ Ignore server certificate errors

This will allow Fiddler to inspect encrypted traffic effectively.
Trust the Fiddler Root Certificate
- Click on “Actions” → “Trust Root Certificate”.
- Follow the on-screen prompts to add Fiddler’s certificate to the trusted certificate store.
This step ensures Fiddler can intercept and decrypt HTTPS traffic without security warnings.




Configure Manual Proxy to Redirect Traffic to Burp Suite
Fiddler allows you to redirect traffic to Burp Suite by setting up a manual proxy.
- Go to Tools → Options → Gateway
- Select “Manual Proxy Configuration”
- Set the Burp Suite listener proxy (default: 127.0.0.1:8080)

This setup routes traffic through Fiddler first, then forwards it to Burp Suite for deeper analysis.
If you haven’t installed Burp Suite yet, you can download it from Here
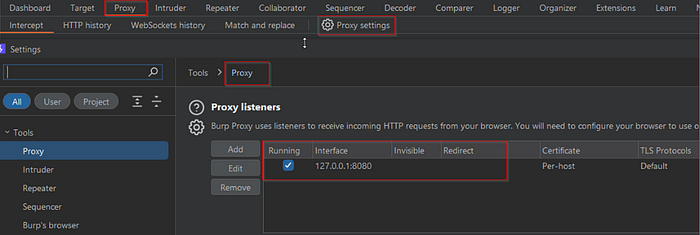
Configure Burp Suite Proxy
- Open Burp Suite and navigate to Proxy → Proxy Settings
- Ensure the proxy listener is active and set to
127.0.0.1:8080.
Configure Fiddler to Exempt System Traffic
- Go back to Fiddler and click on “WinConfig”.
- Select “Exempt None” to ensure only the intended application traffic is intercepted, avoiding unnecessary system traffic.
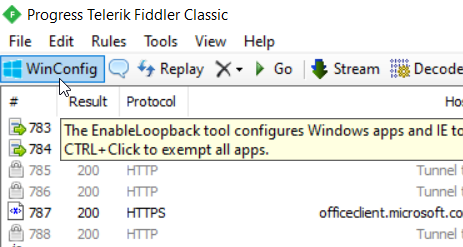
Make sure “Exempt None” is selected. If not, select it and save the changes. Once done, you’re all set!

Now, launch any thick client application and perform actions like login, signup, or any operation that generates HTTP traffic. If everything is set up correctly, you’re good to go!

If you encounter any difficulties or problems, let me know in the comments.
Thanks for your patience. [ Hit some likes :) ]
Sahil Shah.
Get in touch with me here:
Linkedin: https://www.linkedin.com/in/sahilshah3276/
Twitter: https://x.com/sahil3276
Github: https://github.com/sahil3276
